When a logic app is triggered from Sentinel, sentinel sends information about the incident to the logic app. This information includes entities as well.
What are entities?
When alerts are sent to or generated by Azure Sentinel, they contain data items that Sentinel can recognize and classify into categories as entities. When Azure Sentinel understands what kind of entity a particular data item represents, it knows the right questions to ask about it, and it can then compare insights about that item across the full range of data sources, and easily track it and refer to it throughout the entire Sentinel experience - analytics, investigation, remediation, hunting, and so on. Some common examples of entities are users, hosts, files, processes, IP addresses, and URLs.
Entities Format
"relatedEntities":[
{
"id":"/subscriptions/GUID/resourceGroups/RG_NAME/providers/Microsoft.OperationalInsights/workspaces/sentinel/providers/Microsoft.SecurityInsights/Entities/",
"type":"Microsoft.SecurityInsights/Entities",
"kind":"Account",
"properties":{
"accountName":"dhruv",
"upnSuffix":"binobe.com",
"aadTenantId":"TENANT_ID",
"aadUserId":"USER_ID",
"displayName":"Dhruv Jain",
"friendlyName":"Dhruv Jain"
}
},
{
"id":"/subscriptions/GUID/resourceGroups/RG_NAME/providers/Microsoft.OperationalInsights/workspaces/sentinel/providers/Microsoft.SecurityInsights/Entities/",
"type":"Microsoft.SecurityInsights/Entities",
"kind":"Ip",
"properties":{
"address":"185.220.101.46",
"location":{
"countryCode":"DE",
"state":"Brandenburg",
"city":"Schoenwalde-Glien",
"longitude":13.12743,
"latitude":52.61983,
"asn":208294
},
"friendlyName":"185.220.101.46"
}
}
]
Actions supported
Following actions are available for entities in Sentinel:
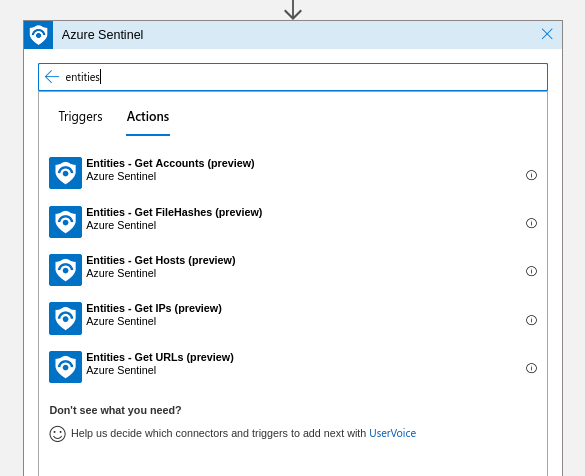
Example: Getting user email'
Users’ information can be fetched from Accounts. Please note that there can be multiple users involved in an incident. In this example, we will fetch users’ email addresses and store them in an array in Logic App. This array can later be used to do other actions as required such as running an AV scan.
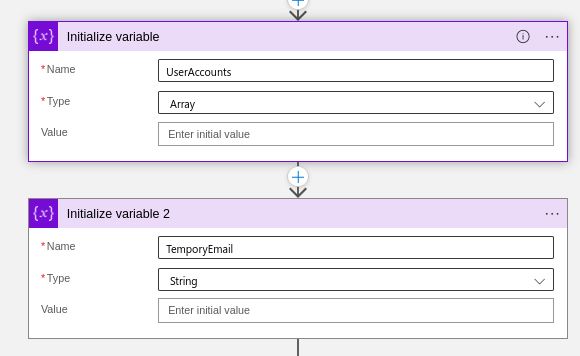
- Let us start by declaring two variables. One will be for storing the array. Second one will be to store email id and crafting it before adding it to the array.
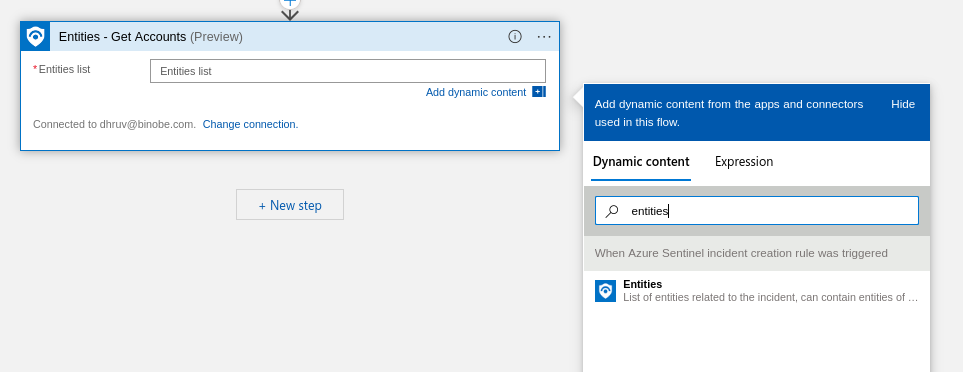
- Next step is getting Account information in Logic App. We will then loop through it and get the relevant information.
- Add a step “Entities – Get Accounts”
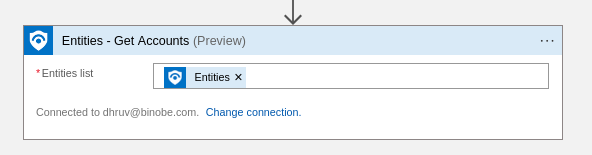
- In the Entities List parameter, add the Entities from the incident
Properties available to you from this step:
If you correlate this data with JSON of entities under “account” kind, you will know that we need to use Accounts Name and Accounts UPN Suffix. So in the next step we will loop over the Accounts and create a string such that
'Account_Name'@'Account_UPN_uffix'
One thing to note is you can not directly do it one step as @ causes issue in the concatenation. So, we divide it into 3 steps:
- Assign Account Name to TemporaryEmail
- Append “@” to Temporary Email
- Append Account UPN Suffix to TemporaryEmail This will give us the email address of the user. In the next step, we will add it to the users email array.
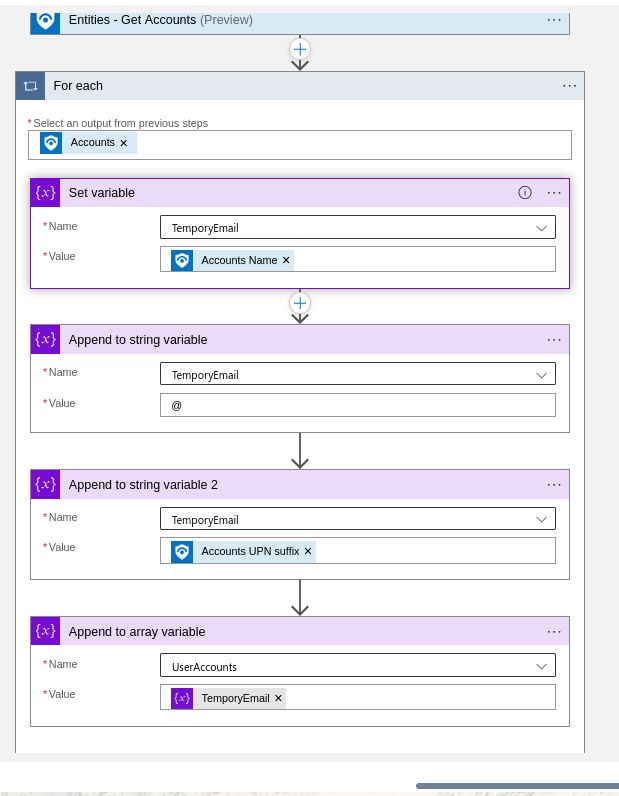
Your email addresses will be stored in UserAccounts Array now.
Conclusion
This concludes our topic on Entites. Hope this session was helpful. You can read more about Entities on https://docs.microsoft.com/en-us/azure/sentinel/entities.